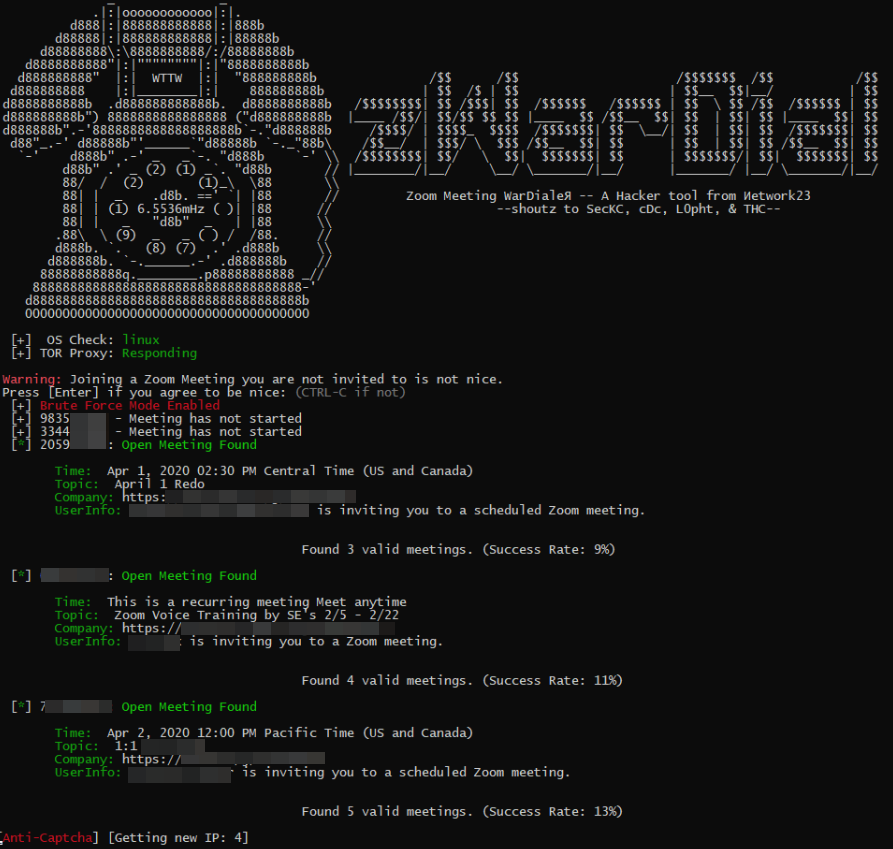
Each Zoom conference call is assigned a Meeting ID that consists of 9 to 11 digits. Naturally, hackers have figured out they can simply guess or automate the guessing of random IDs within that space of digits.
Security experts at Check Point Research did exactly that last summer, and found they were able to predict approximately four percent of randomly generated Meeting IDs. The Check Point researchers said enabling passwords on each meeting was the only thing that prevented them from randomly finding a meeting.
Zoom responded by saying it was enabling passwords by default in all future scheduled meetings. Zoom also said it would block repeated attempts to scan for meeting IDs, and that it would no longer automatically indicate if a meeting ID was valid or invalid.
Nevertheless, the incidence of Zoombombing has skyrocketed over the past few weeks, even prompting an alert by the FBI on how to secure meetings against eavesdroppers and mischief-makers. This suggests that many Zoom users have disabled passwords by default and/or that Zoom’s new security feature simply isn’t working as intended for all users.
New data and acknowledgments by Zoom itself suggest the latter may be more likely.
Earlier this week, KrebsOnSecurity heard from Trent Lo, a security professional and co-founder of SecKC, Kansas City’s longest-running monthly security meetup. Lo and fellow SecKC members recently created zWarDial, which borrows part of its name from the old phone-based war dialing programs that called random or sequential numbers in a given telephone number prefix to search for computer modems.
Comments
Post a Comment